
In this article, you will learn and explore details about what a DDOS Attack mean, how it functions. This write up is basically all you need to grasp the concept of DDOS attacks. DDOS attacks are a primary concern in Internet security today which makes it a very relevant topic to discuss.
DDOS means “Distributed Denial-of-Service“. It can be defined as a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
The latter achieves effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices. In Simple terms a DDOS attack is like an unexpected traffic jam clogging up the highway, preventing regular traffic from arriving at its destination.
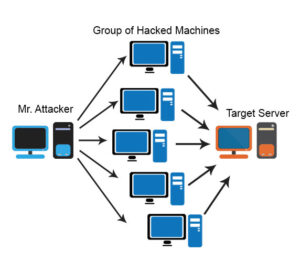
How Does a DDOS Attack Work
A DDOS attack is carried out with networks of Internet-connected machines. These networks consist of computers and other devices (such as IOT devices) which have been infected with malware, allowing them to be controlled remotely by an attacker. These individual devices are referred to as bots (or zombies), and a group of bots is called a botnet.
Once a botnet has been established, the attacker is able to direct an attack by sending remote instructions to each bot. When a victim’s server or network is targeted by the botnet, each bot sends requests to the target’s IP address, potentially causing the server or network to become overwhelmed, resulting in a denial-of-service to normal traffic.
Because each bot is a legitimate Internet device, separating the attack traffic from normal traffic can be difficult.
Stay Ahead of Attackers: How to Identify A DDOS Attack
From a tactical DDOS mitigation standpoint, one of the primary skills you need to have is pattern recognition. Being able to spot repetitions that signify a DDOS attack is taking place is key, especially in the initial stages. Automated applications and AI are often used as helpers, but generally companies need a skilled IT professional to differentiate between legitimate traffic and a DDoS attack.
The following are typical warning signs which could mean a DDOS attack is taking place.
- Reports from existing mitigation devices (e.g., load balancers, cloud-based services)
- Customers report slow or unavailable service
- Employees utilizing the same connection also experience issues with speed
- Multiple connection requests come in from a specific IP address over a short amount of time
- You receive a 503 service unavailable error when no maintenance is being performed
- Ping requests to technology resources time out due to Time to Live (TTL) timeouts
- Logs show an abnormally huge spike in traffic
DDoS vs. DoS Attacks: What’s the Difference?
It’s important to avoid confusing a DDoS (distributed denial of service) attack with a DoS (denial of service) attack. Although only one word separates the two, these attacks vary significantly in nature.
- Strictly defined, a typical DDoS attack manipulates many distributed network devices in between the attacker and the victim into waging an unwitting attack, exploiting legitimate behavior.
- A traditional DoS attack doesn’t use multiple, distributed devices, nor does it focus on devices between the attacker and the organization. These attacks also tend not to use multiple internet devices.
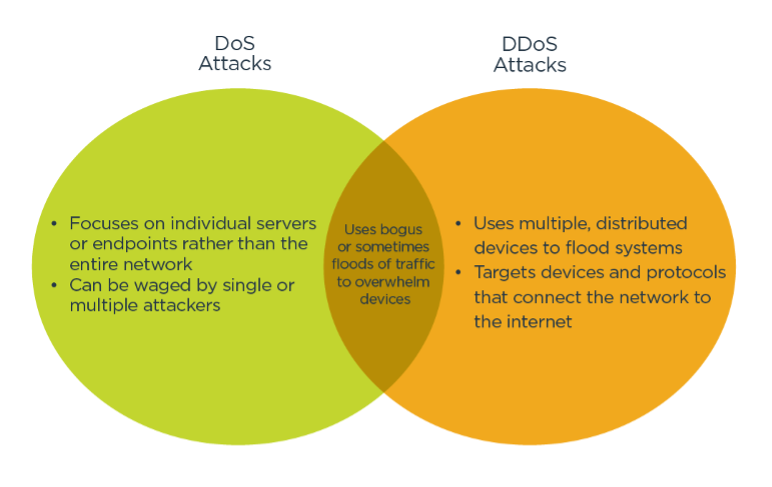
Typical DoS attacks can include the following:
- Single-source SYN floods: This occurs when an attacker uses a single system to issue a flood attack of SYN packets, manipulating the typical TCP three-way handshake. For example, a SYN flood someone might generate using a Kali Linux computer is not a true DDoS attack because the attack being made is only coming from one device. This is the case even if the attacker uses IP address spoofing. A true DDoS attack is generated by network-level devices, for network-level devices. In other words, you use multiple routers or Memcached servers to attack a network.
- The “ping of death”: Years ago, some network drivers contained flawed code that would crash a system if it received an ICMP packet that contained certain parameters.
- The slow loris attack: The slow loris attack is often called a DDoS attack, but because the attack targets a specific server (in this case, a web server) and usually does not use intermediate networking devices, it is typically a traditional DoS attack.
Each of the above DoS attacks take advantage of software or kernel weaknesses in a particular host. To resolve the issue, you fix the host, and/or filter out the traffic. If you can upgrade a server to mitigate an attack, then it doesn’t qualify as a traditional DDoS attack.
Remember, in a DDoS attack, the threat actor adopts a resource consumption strategy. This strategy involves using what appears to be legitimate requests to overwhelm systems which are, in fact, not legitimate, resulting in system issues.
How Long Does a DDOS Attack Last
DDoS attacks vary greatly in length and sophistication. A DDOS attack can take place over a long period of time or be quite brief:
- Long-Term Attack: An attack waged over a period of hours or days is considered a long-term attack. For example, the DDoS attack on AWS caused disruption for three days before finally being mitigated.
- Burst Attack: Waged over a very short period of time, these DDOS attacks only last a minute or even a few seconds.
Don’t be deceived. Despite being very quick, burst attacks can actually be extremely damaging. With the advent of internet of things (IoT) devices and increasingly powerful computing devices, it is possible to generate more volumetric traffic than ever before.
As a result, attackers can create higher volumes of traffic in a very short period of time. A burst DDoS attack is often advantageous for the attacker because it is more difficult to trace.
Evolvement of DDOS Attack
One of the realities of cybersecurity is that most attackers are moderately talented individuals who have somehow figured out how to manipulate a certain network condition or situation. Even though there is often discussion about advanced persistent threats (APT) and increasingly sophisticated hackers, the reality is often far more mundane.
For example, most DDoS attackers simply find a particular protocol. They’ll discover that they can manipulate the transmission control protocol (TCP) handshake to create a flood attack of SYN packets or a particular type of server, such as the memory cache daemon (it is often called “Memcached,” for memory cache daemon).
The Memcached service is a legitimate service frequently used to help speed up web applications. Attackers have often exploited Memcached implementations that are not properly secured, and even those that are operating properly.
Attackers have also discovered that they can compromise IoT devices, such as webcams or baby monitors. But today, attackers have more help. Recent advancements have given rise to AI and connective capabilities that have unprecedented potential.
Like legitimate systems administrators, attackers now have voice recognition, machine learning and a digital roadmap that can allow them to manipulate integrated devices in your home or office, such as smart thermostats, appliances and home security systems.
Why Hire a Professional Hacker from Us
With over 3598 successfully-completed projects and numerous happy clients who have solicited our hacking services, our team of professional hackers is known to many as undoubtedly one of the team of hackers who happen to be on top of their game in the hacking community.
Professional Hacker for Hire is known to take good care of clients as well as their projects seriously with a guaranteed claim their task will be completed and on time. The team makes this claim because, we only accept tasks we are able to complete with no doubts.
We know the ins and outs of DDOS attacks, if you choose to hire us, we can help you detect, prevent or implement these sort of hacks. Our team of experts are more than capable of handling DDOS Attacks
References
There is no good article that doesn’t profit from the knowledge of other blogs and people. We used information from the following sites when we compiled this beautiful peace.



























